Add SSH support for elliptic-curve cryptography aka ECDSA · Issue #4378 · duplicati/duplicati · GitHub

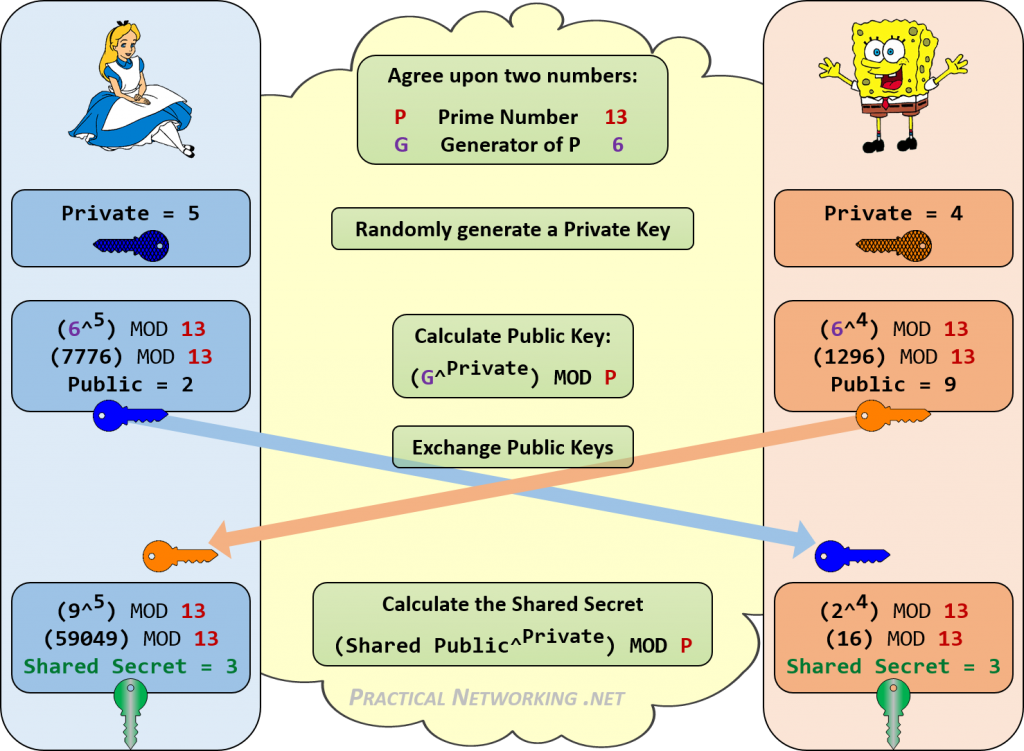
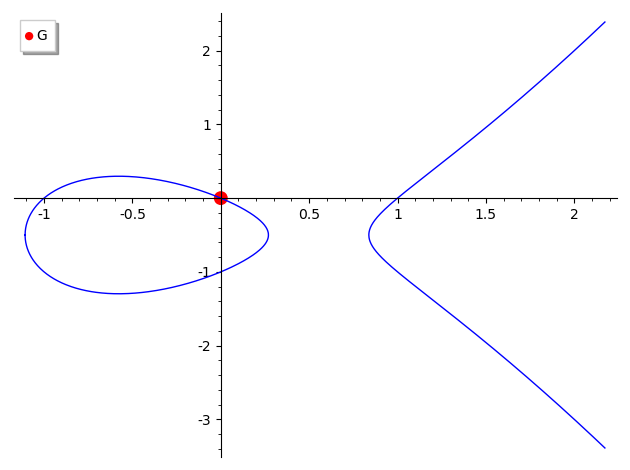
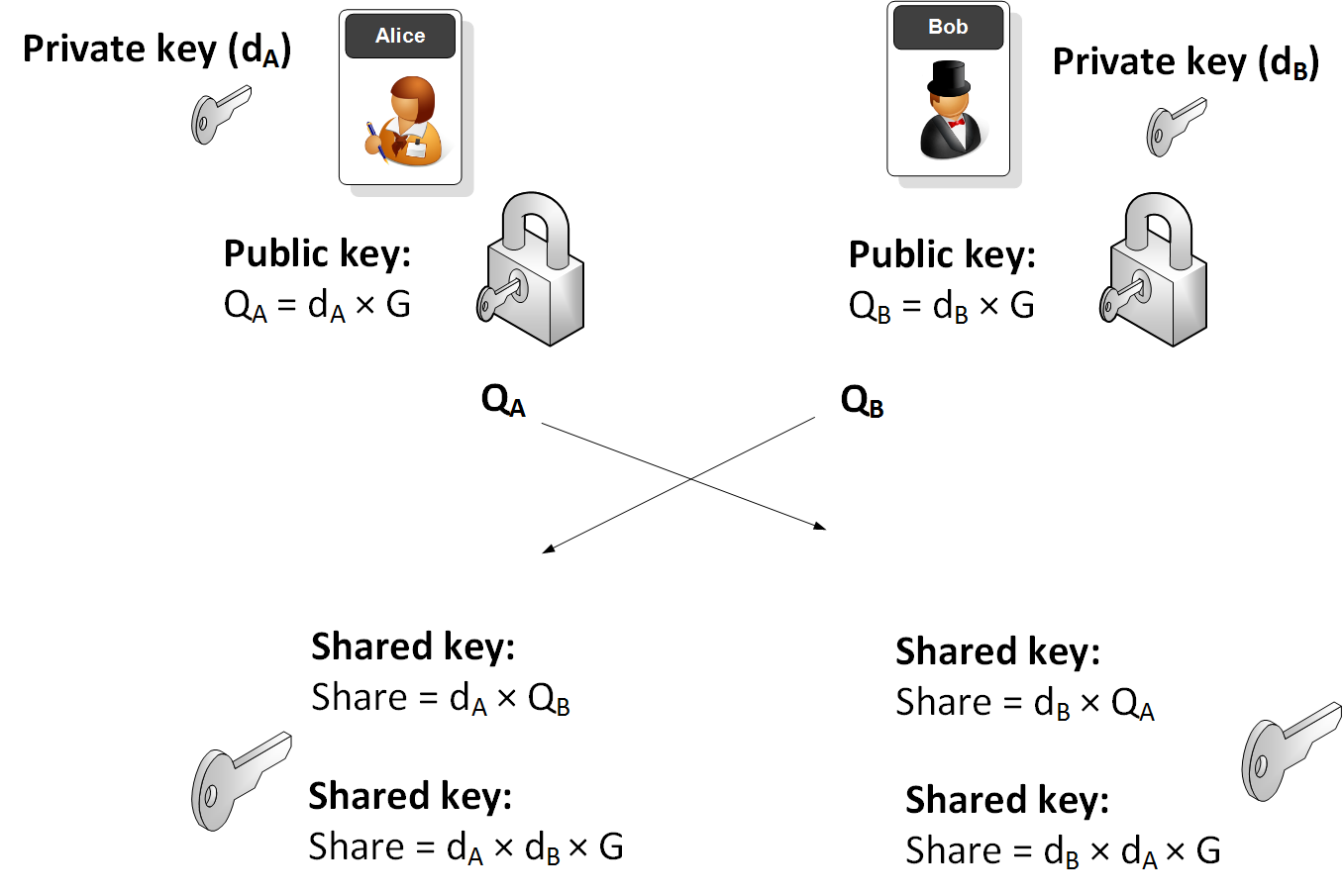
Elliptic Curve Cryptography Basics | Cryptography & Blockchain | by Karthikeyan Nagaraj | Jan, 2023 | InfoSec Write-ups
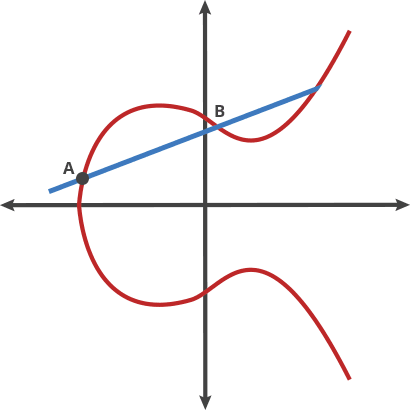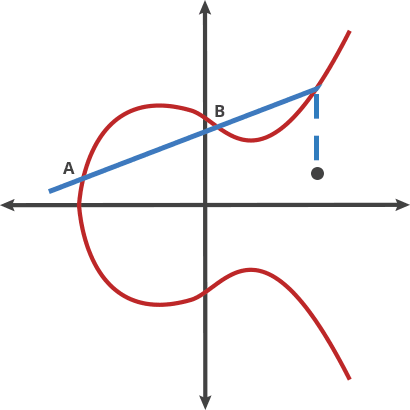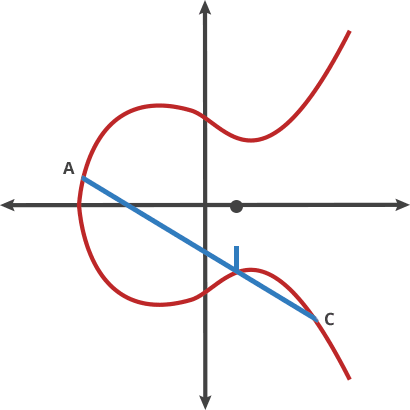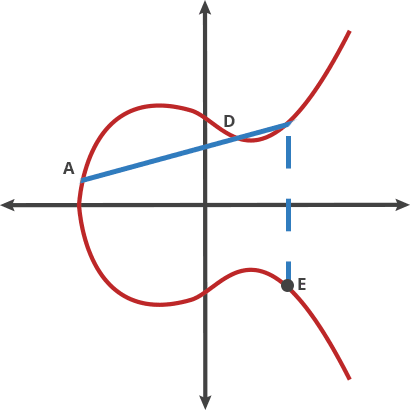
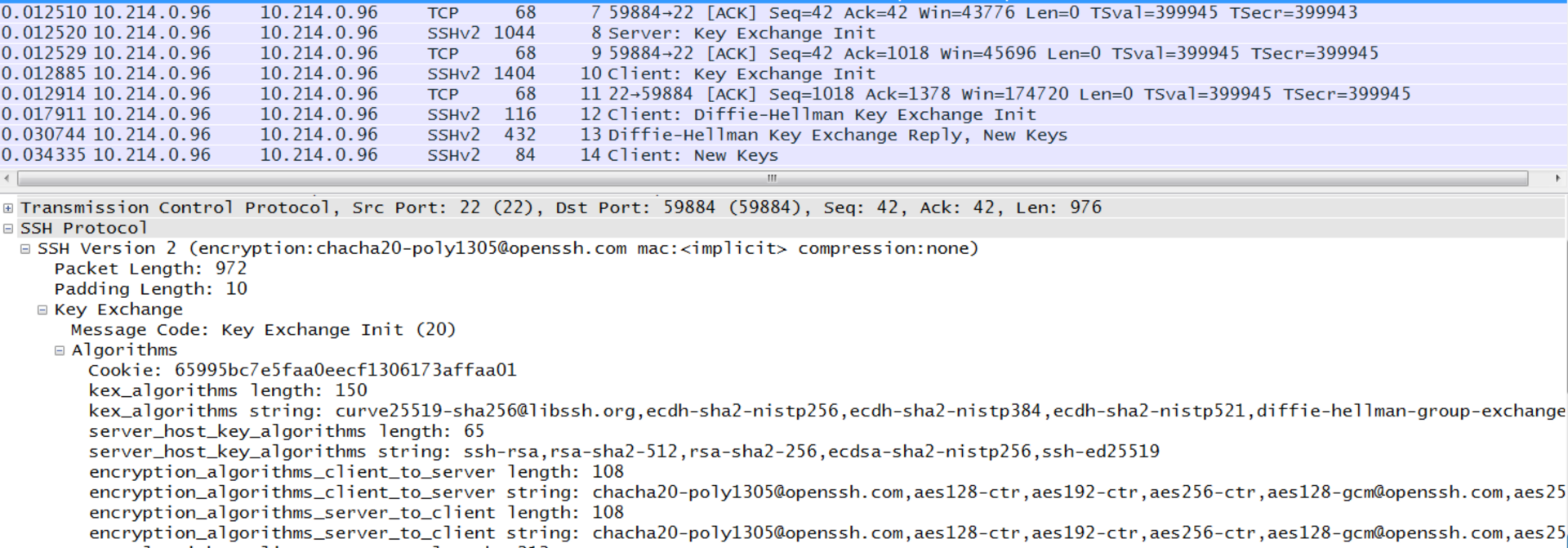
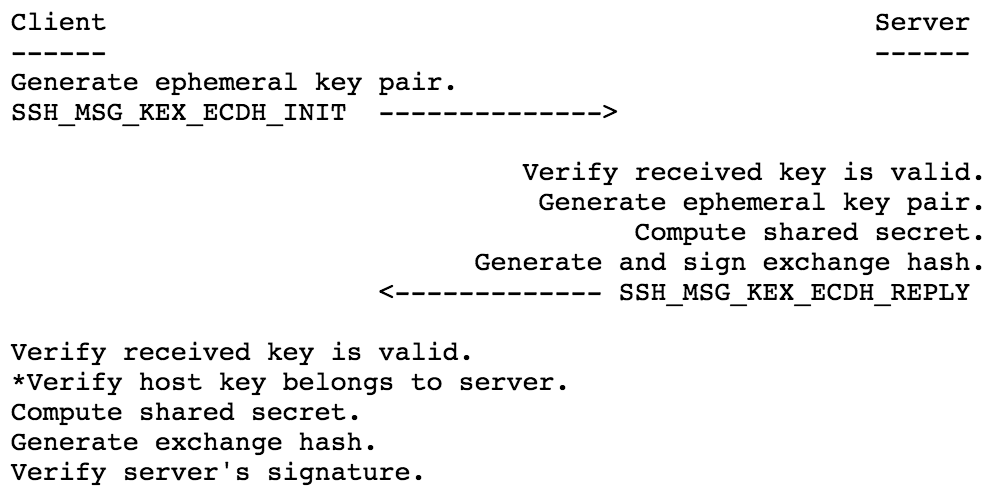
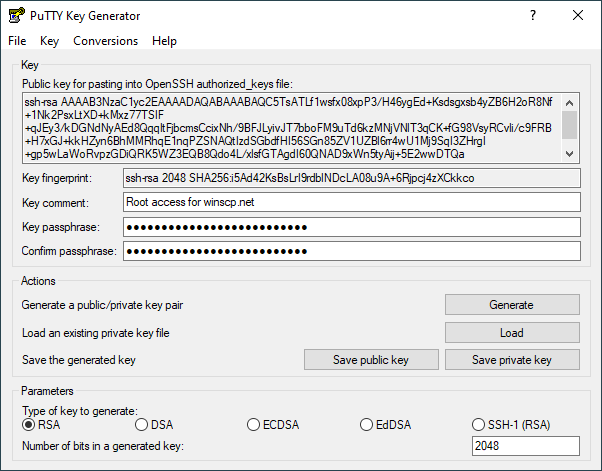
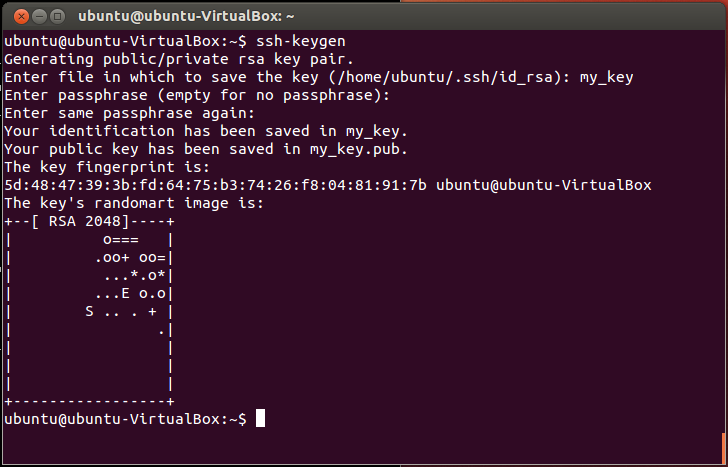
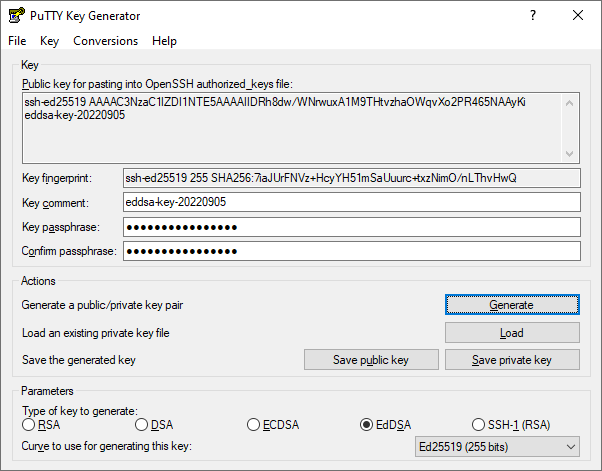
ecc - Is it bad that my ed25519 key is so short compared to a RSA key? - Information Security Stack Exchange

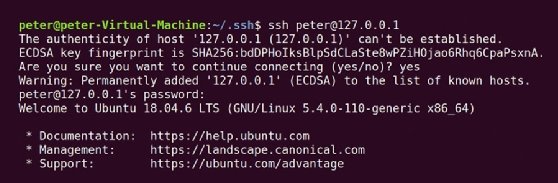
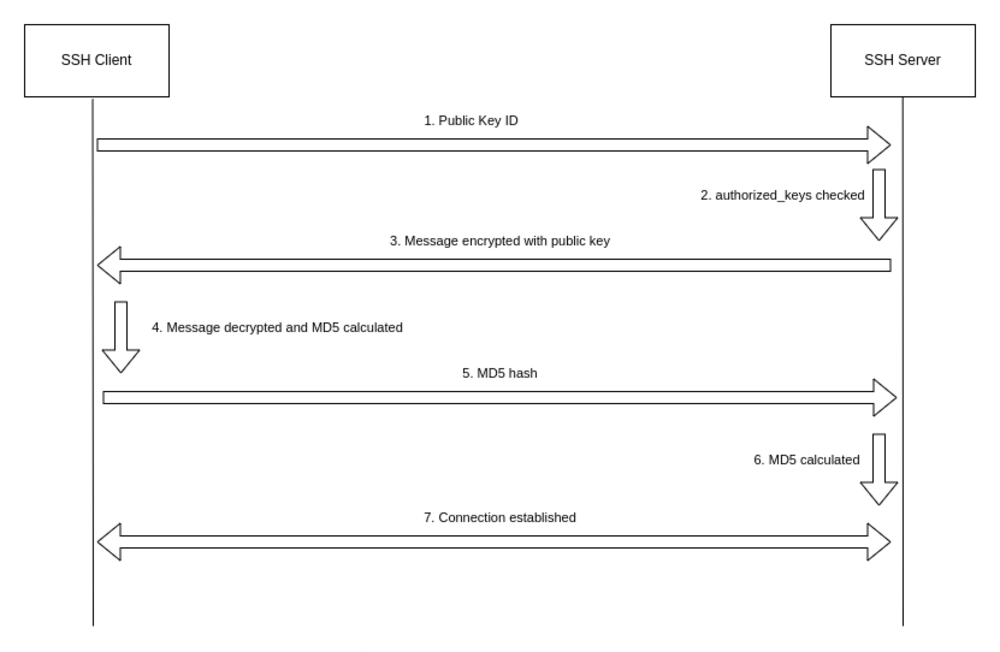
Add SSH support for elliptic-curve cryptography aka ECDSA · Issue #4378 · duplicati/duplicati · GitHub