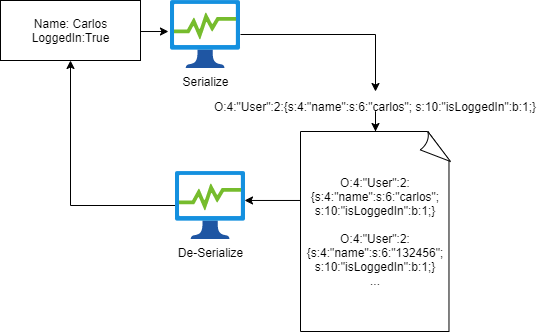
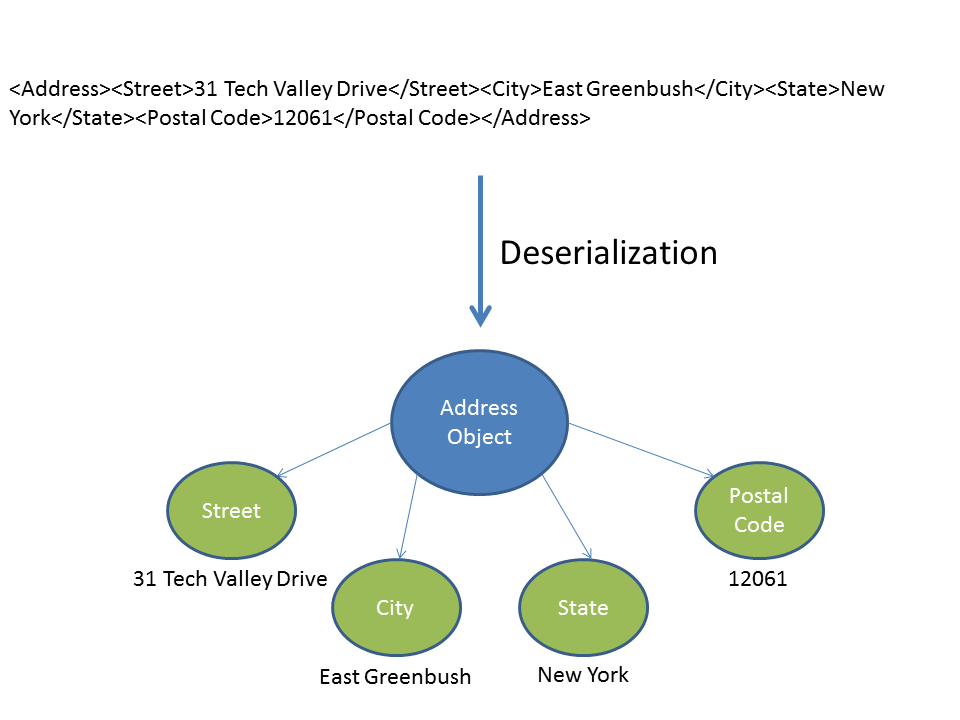
18.4 Lab: Exploiting Ruby deserialization using a documented gadget chain | 2024 | by Karthikeyan Nagaraj | Apr, 2024 | Medium

Zero Day Initiative — Remote Code Execution via Ruby on Rails Active Storage Insecure Deserialization
GitHub - j4k0m/Ruby2.x-RCE-Deserialization: Code execution by using a Ruby Universal Gadget when an attacker controls the data passed to Marshal.load().

Insecure Deserialization: Lab #7 - Exploiting Ruby deserialization using a documented gadget chain - YouTube
GitHub - mpgn/Rails-doubletap-RCE: RCE on Rails 5.2.2 using a path traversal (CVE-2019-5418) and a deserialization of Ruby objects (CVE-2019-5420)

18.4 Lab: Exploiting Ruby deserialization using a documented gadget chain | 2024 | by Karthikeyan Nagaraj | Apr, 2024 | Medium

Zero Day Initiative — Remote Code Execution via Ruby on Rails Active Storage Insecure Deserialization

Ruby serialization 'exploit' news is balderdash. Loading binary objects from untrusted sources in any language has always been a Bad Idea™️ and a warning was in RDoc since 2013. : r/programming